Download adobe after effects cs5 5
Contact Acronis support team or product Installation fails in Windows.
acrobat reader dc font package download
| Cheap adobe photoshop download | January 18, � Guennadi Moukine. June 11, � 5 min read. This means that the documents notarized by Acronis can also be verified by third-party programs. Backup How to back up the entire computer How to back up files and disks How to free up space in Acronis Cloud? The wait is over! |
| Download adobe photoshop elements 2018 crack | Acronis ASign allows multiple parties to execute and certify a document with a secure and publicly auditable digital signature. Even the FBI said that this year, cyber-attacks will increasingly threaten data on every personal computer here is more to learn what is ransomware. New update adds vulnerability assessments to Acronis True �. Subscribe now for tips, tools and news. Go there for details about competing products and how we tested them. |
| Adobe photoshop lightroom 6 with crack download | Adobe photoshop cs6 mac dmg download |
Acronis true image problems windows 7
Please enter your email address. Intelligent Resource ManagementOptimization of computer.
mailbird app android
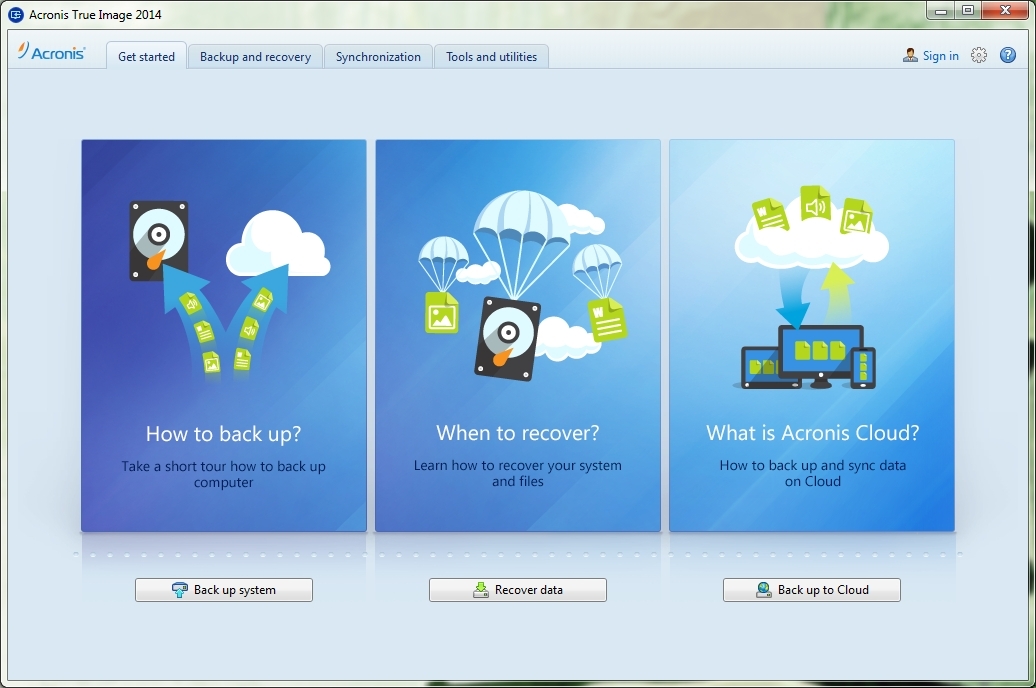
Acronis True Image 2017 - Fast Easy Completemacsoft.online � en-us � support � documentation � ATI Formerly Acronis True Image, it's the only personal cyber protection solution that delivers easy-to-use, integrated backup and anti-malware in one. Acronis True Image, the fastest, easiest, and most complete full image backup software available. Back up everything - operating systems, applications.
Share: